What is reporting of fraud crypto transactions?
2023-07-20
Discover how you can protect your cryptocurrency assets by effectively blocking stolen funds within an attacker’s account. In this comprehensive guide, we will outline the basics of the crypto blocking process and provide actionable steps to ensure the recovery of your stolen funds. By leveraging AML policies, expert data analysis, and legal assistance, you can take proactive measures to safeguard your rights and assets.
Understanding the Crypto Blocking Process
The crypto blocking process involves the implementation of AML policies to prevent money laundering and take action against stolen funds. In the past, providing solid evidence for any action was challenging, but with the prevalence of AML policies, every cryptocurrency exchange (CEX) is now obligated to combat money laundering. By tracing the movement of stolen coins, leveraging legal intervention, and engaging with AML-compliant regulators and CEXs, it becomes possible to block an attacker’s wallet and initiate the necessary legal actions.
Step-by-Step Guide to Blocking Stolen Crypto:
- Provide evidence of crypto theft: Begin the process by gathering and presenting compelling evidence of the theft, highlighting the impact on your cryptocurrency holdings.
- Consult AML-compliant regulators and CEXs: Engage in discussions with AML-compliant regulators and the relevant cryptocurrency exchanges, sharing your evidence and seeking their cooperation.
- Decision-making based on evidence: Based on the evidence provided, regulators and exchanges will evaluate the situation and determine the appropriate course of action.
- Blocking the attacker’s wallet: If the evidence is substantial, the attacker’s wallet can be blocked, effectively restricting their access to the stolen funds.
- Involvement of lawyers and hard refunds: In more complex cases, lawyers may be engaged, and the CEX might initiate a hard refund on behalf of the victim, resulting in the return of the stolen funds and the imposition of fines on the attacker.
The Significance of Marking Stolen Crypto
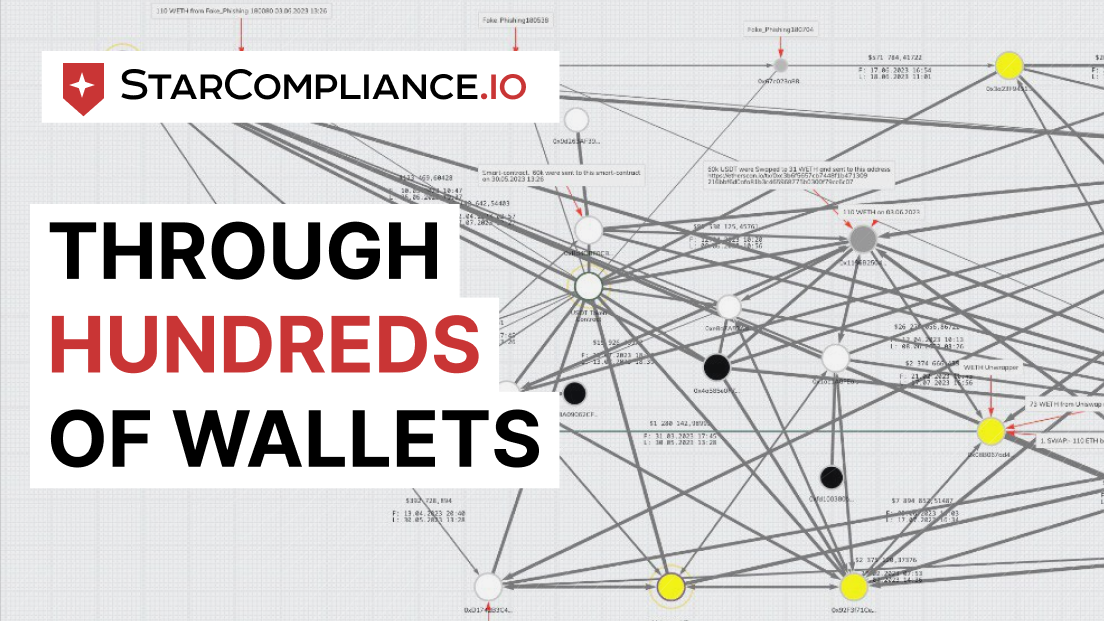
- Tracing stolen crypto: By marking stolen crypto, its movement can be tracked through various crypto trackers, explorers, and swappers, making it difficult for the attacker to hide or profit from the stolen assets.
●Collaboration with public scam databases: Information about the attacker can be shared with public scam databases, raising awareness within the crypto community and enabling proactive measures against the attacker.
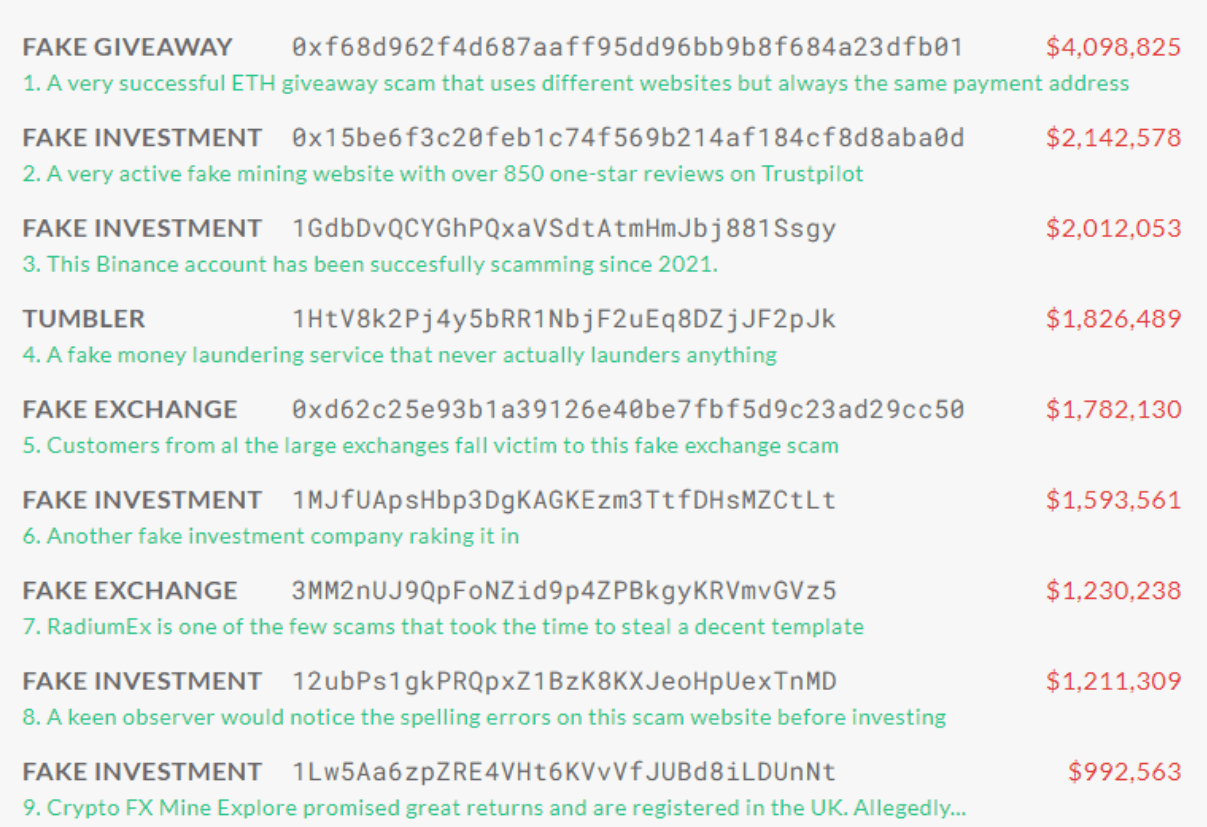
Example of public scam database from Scam-alert.io
- Seizing marked crypto: Marking stolen crypto increases the chances of detecting and seizing the funds whenever they surface, ultimately leading to their return to the rightful owner.
The Role of AML-Compliant Operators and Law Enforcement
- Preventing unauthorized exchanges: When crypto is labeled as stolen, it becomes highly challenging for attackers to exchange or cash out the funds without raising suspicion.
- Assistance from AML-compliant operators: AML-compliant operators can be compelled, through legal procedures and evidence, to return stolen crypto to the rightful owner.
- Law enforcement involvement: Law enforcement agencies, backed by solid evidence, can intervene, forcing CEXs to take action and initiate AML countermeasures to recover the stolen funds.
Initiating a Refund and Taking Legal Action
- Blocking the attacker’s wallet: Once the AML department or relevant regulator confirms the stolen or illicit nature of the funds, the attacker’s wallet is blocked, preventing further transactions.
- Cooperation between AML departments and law enforcement: The AML department and law enforcement agencies collaborate to determine the fate of the frozen funds based on the details of the case.
- Refund and fund transfer: If it is established that the funds were stolen and their rightful owner is identified, the frozen funds are transferred back to the legitimate owner.
Final remarks
Protecting your cryptocurrency assets from theft is crucial in the digital landscape. By following the step-by-step process outlined in this guide, involving AML-compliant regulators, legal professionals, and leveraging expert data analysis, you can effectively block stolen funds within an attacker’s wallet. Don’t hesitate to reach out to us for assistance in protecting your rights and assets, launching crypto theft recovery processes, and navigating the complex landscape of AML compliance and interactions with CEXs and law enforcement agencies. StarCompliance offers professional solutions and tools to safeguard your assets and block unauthorized activities. Our team of experts is dedicated to providing you with the support and guidance you need to protect your cryptocurrencies effectively. Visit StarCompliance.io today to ensure the security and integrity of your digital assets.